About Aws Backup
Wiki Article
How Data Protection can Save You Time, Stress, and Money.
Table of ContentsData Protection Can Be Fun For AnyoneFascination About S3 Cloud BackupProtection Against Ransomware Can Be Fun For EveryoneThe Best Guide To Aws Cloud BackupThe Greatest Guide To Aws Backup
Keeping multiple vendors and also platforms along with common computing has put fantastic strain on IT divisions. Going onward, data protection need to have the ability to adapt to these already intricate situations. Information protection techniques are created to secure data, preserve personal privacy as well as avoid information loss and also corruption without trading them for evaluation as well as evaluation.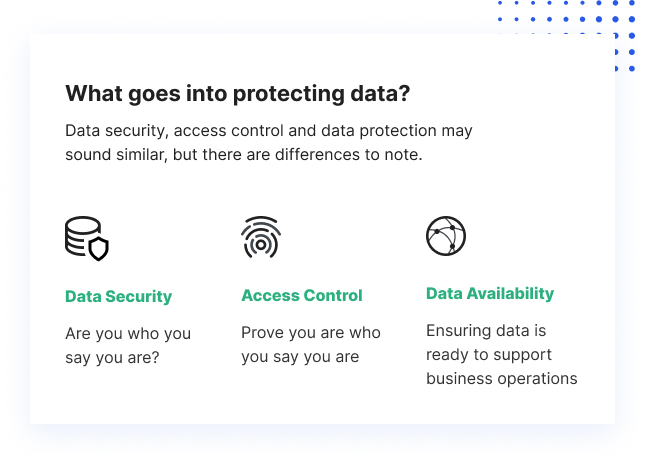
Information erasure methods likewise confirm the data can not be recovered. Accessibility management controls make sure information honesty by restricting access to digital properties.
After all, a lot of the world's interactions as well as organization takes place in the cloud or through individual devices in remote job atmospheres. The most effective information security services combine durable safety and security actions with human procedures as well as workflows. The total goal: to ensure information defense is considered early during the digital details life cycle.
The Buzz on Ec2 Backup
Information security is everyone's business, so, it's likewise important to make sure normal, ongoing security awareness training is part of your information security strategy. Information personal privacy specifies who has access to information, while information defense supplies tools and also policies to in fact restrict accessibility to the information.It plays an important role in organization procedures, advancement, and funds. By shielding information, firms can stop information violations, damage to credibility, and can much better meet regulatory needs. Information protection solutions count on technologies such as information loss prevention (DLP), storage with integrated information security, firewalls, encryption, and also endpoint protection.
A data protection strategy is important for any organization that collects, handles, or stores sensitive data. Information protection principles aid protect information and make it readily available under any circumstances.
The smart Trick of Ransomware Protection That Nobody is Discussing
Here are vital data administration facets pertinent to data defense: making certain users can access and also utilize the data called for to carry out business also when this data is lost or harmed. entails automating the transmission of critical data to offline and on the internet storage. involves the appraisal, cataloging, and security of details properties from various sources, consisting of facility outages and disturbances, application as well as individual mistakes, maker failure, and malware and virus attacks.Information personal privacy is generally applied to individual wellness info (PHI) and directly identifiable details (PII). Data privacy problems apply to all sensitive details that organizations manage, including that of customers, investors, and employees.
It avoids wrongdoers from having the ability to maliciously use information and also helps ensure that organizations meet governing needs. Information protection policies regulate how particular information kinds are collected, sent, and made use of. Individual information consists of different kinds of details, consisting of names, pictures, email addresses, savings account details, IP addresses of personal computers, and biometric data.

10 Easy Facts About Aws S3 Backup Explained
In addition, each legislation additional hints consists of various provisions that might relate to one case but not an additional, and all regulations undergo modifications. This level of complexity makes it difficult to implement conformity constantly and also suitably. Both data defense and privacy are essential as well as the 2 frequently come together, these terms do not represent the same thing.Information privacy defines the plans that information defense devices and procedures employ. You can restrict accessibility with information securities while still leaving sensitive information prone.
For protection, it is up to the companies handling information to ensure that it stays private. Conformity guidelines show this distinction and are developed to assist make certain that users' privacy demands are passed by business. When it comes to securing your information, there are many storage as well as administration choices you can select from (s3 backup).
Below are several of one of the most frequently made use of practices as well as modern technologies: an initial action in data protection, this includes uncovering which information sets exist in the organization, which of them are service essential as well as which consists of delicate data that could be based on conformity laws (aws cloud backup). a set of approaches as well as devices that you can make use of to avoid information from being swiped, lost, or mistakenly removed.
The Ultimate Guide To Rto
Cloudian's Hyperstore supplies up to 14 nines of sturdiness, low price allowing storage of large volumes of information, and quick accessibility for marginal RTO/RPO. Discover extra in our overview to.Report this wiki page